Greetings to you, my friend.
I know this will come as a surprise to you, because you do not know me. My name is Abdul Al-Shallah and I am the son of a deposed government official in Nigeria.
Sound familiar? It?s a boilerplate opening for one of the most common scams in the known world ? the Nigerian scam, also known as the ?419 scam? or the advance fee scheme. The elements are always the same: someone (preferably royalty or some sort of official) has come into a lot of money, but needs another person outside of the country to use their money for a bribe (or to pay legal fees among other means) to spring the money free. The result is also predictable, with a wire transfer to a con artist?s account and a fake check that confirms a scam has taken place.
This scam is a hallmark of the Internet, but it?s actually much older than that ? the advance fee scheme in its modern incarnation dates back to the early 1980s, and various forms can be traced back to before the 20th century. The reason that it sticks around, unsurprisingly, is because it never ceases to swindle millions of dollars from duped victims. The scheme, and many others like it continue to flood inboxes daily, often hitting the Spam folder before you ever lay eyes on it, waiting for a more trusting person to make a trip to the Western Union.
But that?s not to say that Internet scammers are resting on their laurels and leaving their dirty work to these classic methods. As Internet users become more sophisticated (and laugh at the advances of the forlorn Nigerian prince or similarly befallen individual), the chances of finding a willing innocent victim slowly dwindles. Like any other industry, scammers are looking for smarter, more efficient ways to reach their big payouts and to keep their ?businesses? running smoothly, so they are forced to adapt and reach new extremes to get their money.
Now, security experts are seeing disturbing trends among scammers that make the old schemes appear to be child?s play. Appealing to the emotional pull of a victim is now just part of the scheme, which now includes familiarity dupes and long-term schemes to raid a bank account. These cons are more targeted, more ruthless and can take out even large corporations and entire governmental programs. There?s a new evolution in Internet con artistry, and it?s putting everyone at risk.
Check out the four new and scary ways con artists are getting their money on the Internet, and real-life examples of how they work.
What do you think of these schemes? Let us know in the comments.
The long con
In the past few years, ?spear-phishing? has risen to become one of the biggest trends in online scamming. A play on the hacking technique ?phishing,? spear-phishing is a technique that con artists use to specifically target individuals or companies and gain access to information or bank accounts. This method has also become the tactic du jour for cyber criminals interested in attacking big business or government officials. But, that doesn?t mean spear-phishing is too advanced for the regular user.
In a spear-phishing scenario, a hacker is able to crack into an inbox of an unsuspecting victim. But, instead of doing a smash-and-grab and gathering as much information as possible, the criminal takes his time ? akin to casing a house before a robbery. Then, the hacker masquerades as an email account of a relatively important company, like Bank of America. The hacker then sends a personalized email explaining to the victim that her account has been compromised, including the victim?s account number to establish credibility, and urges her to quickly change her name and password via a link provided in the email. The victim is duped into downloading nasty malware onto her computer, and the con artist is able to walk away with cash in his pocket.
?They dig deeper down. They know who you?re talking to and what the subject matter is about,? ?says George Waller, executive vice president at New Jersey-based cybersecurity software corporation StrikeForce Technologies. ?Then they?ll most likely spear-phish you with a malicious attachment or direct you to a site with a malicious download on it.?
And, at times, spear-phishing can drift into the absurd, like the story told by?ESET?Security Evangelist?Stephen Cobb of hackers who had used a victim?s account to steal his money by stealing his heart. The hackers broke into a wealthy victim?s Gmail account and began rifling through the inbox. While reading the emails, they discovered the victim enjoyed frequenting dating websites, looking for a potential long-term mate. The hackers found the victim on the website and posed as a beautiful woman who was romantically interested in him. The hackers proceeded to forge a long-term relationship with him before begging for ?emergency? money to be wired via Western Union. The victim readily accepted and the con went off without a hitch.
?This technique is particularly pernicious because it doesn?t immediately look like a scam,? Cobb says. ?This isn?t some stranger saying, ?Hi, you do not know me, but I have come into a large sum of money.? You?ve gotten to know this person on social media and they?ve targeted you that way.?
The authority dupe

Hackers aren?t only making emotional appeals, but also using fear or urgency to manipulate victims into giving over their identities and bank accounts. Waller explains that one of the common methods is that hackers use this tactic while posing as a common workplace resource, like a payroll company. Hackers can lure victims by claiming (ironically) a security breach or emergency that requires a change of password or download of a file. At that point, victims begin to divulge critical information or, perhaps even worse, download malware onto their computers that allows hackers to infiltrate computers and unlock even more information. Victims are tricked into believing they?re securing their systems and tying up loose ends, not compromising them.
?We?re all tied to the Internet and it?s part of our daily lives,? Waller explains. ?We?re looking at it to check our emails and to conduct our business, but if you?re multi-tasking and you see something you recognize that?s actually a piece of spyware, it only takes one click. One click, and you?re infected.?
Another notable way that con artists take advantage of victims doesn?t directly involve a computer at all, but instead relies on a victim?s?lack of knowledge?about technology to earn a quick dollar. Cobb explains that one of the most common scams the ESET teams see are ?IT phone calls,? where con artists call computer owners pretending to be Microsoft or Apple support techs and convince victims that their computers are riddled with ?errors? ? standard computer functions that can look threatening to an uninitiated computer user. They will even go so far as to walk the victim through a series of tests to ?prove? the infections exist on the computer, even though many of them are common. By feigning emergency (and following a script), con artists can snag a quick $50 or so from concerned people.
?This scam is going on everywhere in the English-speaking world,? Cobb explains. ?And everybody who has Windows has gotten a problem before. The pitch for the product is constantly evolving and it really tricks people.?
The puppet
Hackers are posing as friends, authority figures, and they?re even pretending to be you. One of the easiest ways hackers can trick victims is by posing as a real friend or relative of someone they know ? a type of hyper-specialized spear-phishing that chooses new marks by consulting information from a previous victim. Con artists, through a key-logger or malware, can figure out their next targets by simply looking at emails. The former victim?s closest friends are usually the easiest targets, as it is simple to convince them to open a suspicious file or link. As the new crop of users get conned, they create new pools by which a hacker can find new victims. In this vicious cycle, it turns those who fall for scams into tools to be used against the people they care about most.
?I think it?s a natural evolution for the scammer,? Cobb says, ?Spam in general is all about volume ? you have to send out large number in order for it to work. But now, the numbers games aren?t working and hacking costs money, so putting more time into a victim is becoming more lucrative. Why try to target someone for a wire transfer who has never done a wire transfer? Find someone who knows how to do a wire transfer and has money, and it?s worth the time to work that person.?
This technique was actually recently used on Waller himself while he was at his own company, no less. As an executive that works frequently with local shipping services, Waller wasn?t surprised to find that USPS sent him an email one day explaining that a package missed delivery and needed to be picked up. The email looked legitimate, and included directions to his nearest post office (listing a known address three blocks away) and a link to the receipt. Waller was certain his company didn?t have any outstanding orders or package deliveries, and remained suspicious of the email. Still, he clicked the email?s link anyway ? and it turned out to be malware.
?This isn?t even a sophisticated attack. This is just a standard phishing attack,? Waller said, ?But if you?re a larger company or a person, it?s easy to see how someone can be deceived by all of this.?
The bait and switch

Of course, nothing does quite as well as an updated version of the classic bait and switch ? a con artist promising one piece of information and instead providing something unwanted such as a trojan or malware. Bait and switch operations are finding a niche in the Internet, where it is easy to pass off a malicious piece of software as a PDF or other file. Waller spoke of a group of hackers that had bought the email addresses of thousands of CFOs on the black market and was able to successfully bait them into downloading malicious software. Using the bought names, the hackers posed themselves as the IRS and sent emails to everyone, claiming that the enterprise tax codes for the year had changed. The email offered a ?handy? PDF of all of the changes which, of course, was infected with a keylogger. After the CFOs unwittingly downloaded the harmful software, the keylogger set to work ? analyzing the keystrokes until it was able to gather the usernames and passwords of each companies? payroll system. That was when the magic happened.
?The hackers picked out CFOs that had several hundred to several thousand employees on purpose because those companies always experience a large turnover of full-time and contracted employees,? Waller explained. ?The hackers were able to log in to the payroll service as the CFO and add a few extra payees to the account without attracting any suspicions.?
This technique occurs on a larger scale in the classic con artist technique of the dubious poll. Companies of varying repute are always advertising online polls and surveys that promise something free ? whether it be an iPad or a cruise to the Bahamas. Users can take these polls online with the promise of a cash payout or fancy prize on the horizon, only to be goaded into a high-pressure situation where they must either sign up for multiple subscriptions or buy additional products in order to get their ?free? reward. This scheme has been used across other media, including phones, but it remains one of the most persistent and successful scams. Cobb attributes the technique?s profitability to the ongoing economic crisis throughout the world.
?In an?economy?where a lot of people are?underemployed?and looking for extra money, a lot of people will be interested in a $1000 Wal-Mart Survey,? Cobb says. ?And, people think that it?s not really free money because they?re?convinced?they?re working for it. They can convince themselves that what they?re doing is okay.?
How to stay safe
The world of cyber scams isn?t only constantly evolving ? it?s relying on a variety of old and new methods to keep the income of cash flowing. This is just a fraction of the kind of schemes that are happening on the Internet today, and only related to email. Scammers are constantly trolling places like Craigslist, message boards and even Facebook groups to make a quick dollar off of unsuspecting people, and there?s a lot at stake.
As always, when avoiding these con schemes, there?s no substitute for good old fashioned common sense. The better that you as an Internet user become at detecting and fending off scams, the less likely you will find yourself upset at the hands of a manipulative con artist.
It?s simple enough to find out whether something is a scam by doing a routine search on Google when any suspicious activity appears in your mailbox. If something has come up in the recent past to indicate that the email you?re reading is actually a piece of malware or a scam, it will likely show up on message boards or in blog posts of security firms. It?s also a smart idea to research anyone you do not know who has contacted you or requested your friendship on a social network. Knowledge, in this case, truly is power.
Cobb agrees that it?s best to be skeptical of your surroundings, and also cautions others to be aware of what they put on social media. The more valuable information a user puts on a public social media profile like Facebook or Twitter, the easier it is to not only break into accounts but also dupe you into believing a scam?s authenticity. So, refrain the next time you think about putting your entire family tree or the history of places you went to school on your public timeline.
?People just don?t realize how helpful over-sharing in social media is to bad people,? Cobb says. ?We talk to people about not sharing too much because it?s?embarrassing? but there?s also an exploitation factor. Use the technology with an understanding that there are people out there who are working all the time to exploit you.?
Waller advises that every user maintain a comprehensive security system that blocks all forms of attacks, including keystroke-logger protection and anti-virus. Because software solutions rarely cover all bases, it?s also important that you secure available programs with a reliable two-factor authentication system like Google Authenticator. A combination of apps and steady vigilance will ensure that hackers won?t be able to sneak into your important accounts unannounced.
?You need to look for proactive approaches to all of this, because the deceptiveness that occurs every day is incredible,? Waller says.
And never, ever go to a Western Union and wire cash unless you know what you?re doing. Ever. Seriously. Just don?t.
Image Credits: Paul J. Richards/Getty Images, Jeff J Mitchell/Getty Images, Mario Tama/Getty Images
Source: http://thenextweb.com/insider/2013/01/20/four-new-ways-online-scammers-are-taking-your-money/
Kerri Strug Ledecky Nadia Comaneci Rebecca Soni Snoop Lion London 2012 Table Tennis badminton
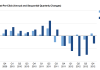 One of the reasons that Google’s shares might have popped about 5 percent in after-hours trading is evidence that the company is stabilizing declines in cost-per-click. The closely watched metric is a measurement of how much advertisers are paying on average when consumers actually click through on paid search keywords or on other ads. It declined dramatically throughout 2012, raising concerns that the shift toward searches on smartphones was cannibalizing pricier ads on the non-mobile web. Cost-per-click was up 2 percent quarter-over-quarter, but down 6 percent year-over-year, according to today’s earnings. If you exclude the impact of foreign exchange fluctuations, they were up 1 percent quarter-over-quarter, but down 4 percent year-over-year, according to the earnings call. While the annualized declines don’t look great, they’re far lower than year-over-year declines from the second and third quarter of last year, which were 16 percent and 15 percent respectively. While Google CEO Larry Page and Senior Vice President Nikesh Arora didn’t really explain what helped slow declines in the last quarter, both were optimistic about prices for mobile ads. “We’re in uncharted territory in these things because of the rapid rate of change,” Page said on the earnings call. “The CPCs will improve as these devices improve.” He later elaborated as analysts asked two or three variations on this question (most of which he frankly evaded). “I don’t think this is a long-term problem,” he said. “As I’ve said before, there are a lot of advantages to mobile. You know the location of the user.” Facebook CEO Mark Zuckerberg has said he’s similarly hopeful about mobile ads. The company has been aggressively pushing app install ads and sponsored stories in the mobile news feed throughout the winter. But we won’t know how well these have done until the company reports earnings next week on Jan. 30. At our conference TechCrunch Disrupt back in September, he said on-stage, “I?m really optimistic. It?s more like TV than the Web. The ads we run on mobile perform better than the right-hand ads do on the site.”
One of the reasons that Google’s shares might have popped about 5 percent in after-hours trading is evidence that the company is stabilizing declines in cost-per-click. The closely watched metric is a measurement of how much advertisers are paying on average when consumers actually click through on paid search keywords or on other ads. It declined dramatically throughout 2012, raising concerns that the shift toward searches on smartphones was cannibalizing pricier ads on the non-mobile web. Cost-per-click was up 2 percent quarter-over-quarter, but down 6 percent year-over-year, according to today’s earnings. If you exclude the impact of foreign exchange fluctuations, they were up 1 percent quarter-over-quarter, but down 4 percent year-over-year, according to the earnings call. While the annualized declines don’t look great, they’re far lower than year-over-year declines from the second and third quarter of last year, which were 16 percent and 15 percent respectively. While Google CEO Larry Page and Senior Vice President Nikesh Arora didn’t really explain what helped slow declines in the last quarter, both were optimistic about prices for mobile ads. “We’re in uncharted territory in these things because of the rapid rate of change,” Page said on the earnings call. “The CPCs will improve as these devices improve.” He later elaborated as analysts asked two or three variations on this question (most of which he frankly evaded). “I don’t think this is a long-term problem,” he said. “As I’ve said before, there are a lot of advantages to mobile. You know the location of the user.” Facebook CEO Mark Zuckerberg has said he’s similarly hopeful about mobile ads. The company has been aggressively pushing app install ads and sponsored stories in the mobile news feed throughout the winter. But we won’t know how well these have done until the company reports earnings next week on Jan. 30. At our conference TechCrunch Disrupt back in September, he said on-stage, “I?m really optimistic. It?s more like TV than the Web. The ads we run on mobile perform better than the right-hand ads do on the site.” According to a
According to a  It?s been cold around here lately. The kind of cold that has me dreaming of jumping on a plane to a tropical destination where I can swim in a warm sea or lounge by an outdoor pool. And then, my daydreaming brings me closer to home and I start thinking about the possibility of installing a swimming pool in my own backyard to take advantage of the nicer months of the year.
It?s been cold around here lately. The kind of cold that has me dreaming of jumping on a plane to a tropical destination where I can swim in a warm sea or lounge by an outdoor pool. And then, my daydreaming brings me closer to home and I start thinking about the possibility of installing a swimming pool in my own backyard to take advantage of the nicer months of the year.

